Disclaimer!!!
The information provided in this blog is to be used for educational purposes only. All of the information in this blog is meant to help the reader to develop a hacker defense attitude in order to prevent the attacks discussed. In no way should you use the information to cause any kind of damage. Hacking is a crime and I am not responsible for the way you use it.
Intro
This blog post is going to be about JWT again. But today, we will take a look at different tools that we can use when working with JWT.
Also, let’s remind one thing. JWT HS256 is calculated using a secret. The exact format of the calculation is:
HMACSHA256( base64UrlEncode (header) + "." + base64UrlEncode (payload), secret)If we have JWT token, and the header and payload, the secret can be brute forced to obtain the full JWT token. If the secret can be brute forced then the attacker could sign his own JWT tokens.
jwt-cracker
This tool is an HS256 JWT token brute force cracker.
Usage:
jwt-cracker <”token”> [<alphabet>] [<maxLength>]Requirements: This script requires Node.js version 6.0.0 or higher
So let’s install it.

Let’s check the version:

Let’s install npm as well:
Now, we can install jwt-cracker:
npm install --global jwt-cracker
The tool’s installed so let’s take a look at an example. Imagine we found the following token:
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6IkpvaG4gRG9lIiwiaWF0IjoxNTE2MjM5MDIyfQ.it4Lj1WEPkrhRo9a2-XHMGtYburgHbdS5s7Iuc1YKOEWe can try to crack the secret using jwt-cracker and passing the token value:
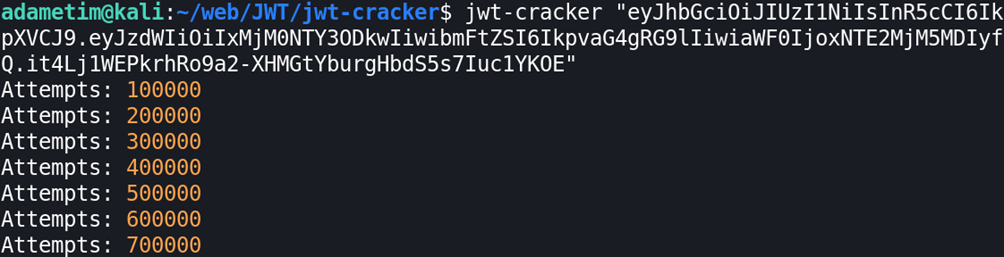
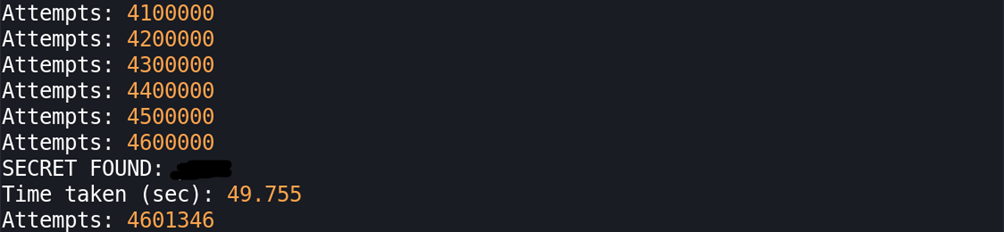
As you can see from the above, it took 4601346 attempts to find the secret. This is pure brute-forcing method which means that you try every possible combination of the characters provided.
jwt_tool
Password cracking method that is used more often is called a dictionary (wordlist) attack. It means that you have a huge wordlist with millions of words and you put each word to the position of the secret and finding out if the word is the actual password.
jwt_tool is a python toolkit for validating, forging, scanning and tampering JWT tokens.
Usage:
jwt_tool <JWT>Let’s download the tool from https://github.com/ticarpi/jwt_tool:
Give the python script execute permission:
To use a wordlist attack, you need to specify two more options:
-C: to crack (crack key for an HMAC-SHA token (specify -d/-p/-kf)
-d <dictionary>: to specify a dictionary
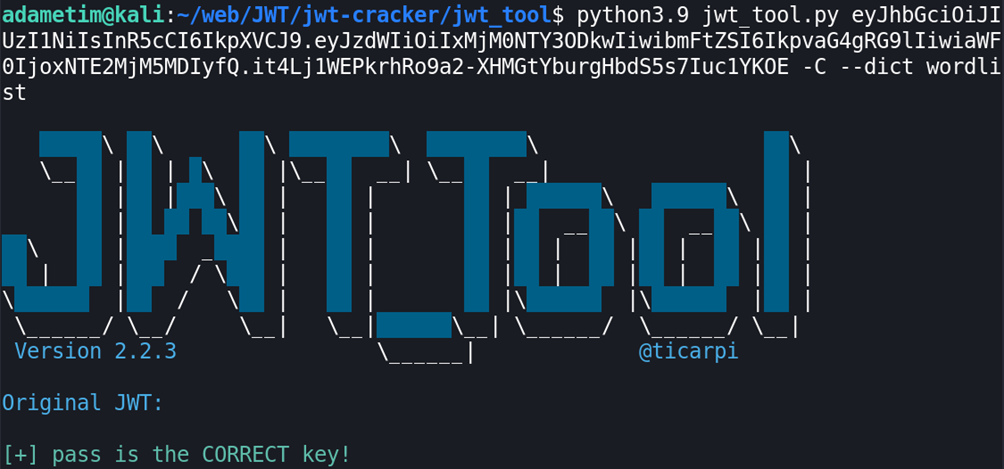
As you can see from the above, we found the correct key.
Since the secret key used for signing the token is known, it could be used to create a valid token. This means that once you find the JWT secret, you can tamper the token to your liking.
When tampering the token, let’s first look at how the token actually looks:
jwt_tool <token>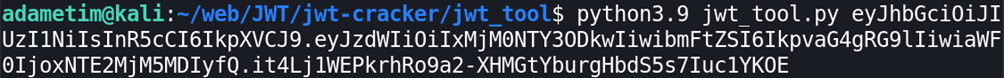

Let’s try to tamper this token using the -T option:


As you can see from the snapshot above, it brings you to the interactive mode where you can choose how to change the token.
The tool has many options, please refer to the help menu to view all of them:
That’s it for this part. Thank you for reading this and see you at the next blog post!
All credits go to Paradox (https://tryhackme.com/p/Paradox) who has created this excellent room. You can find it at https://tryhackme.com/room/zthobscurewebvulns