Disclaimer!!!
The information provided in this blog is to be used for educational purposes only. All of the information in this blog is meant to help the reader to develop a hacker defense attitude in order to prevent the attacks discussed. In no way should you use the information to cause any kind of damage. Hacking is a crime and I am not responsible for the way you use it.
Task 1: Intro to ZAP
OWASP ZAP (Zed Attack Proxy) is a security testing framework much like Burp Suite. It is used to test web applications. It’s completely open source and free. There is no premium version.
Benefits over Burp Suite:
- Automated Web Application Scan: This will automatically passively and actively scan a web application, build a sitemap, and discover vulnerabilities. This is a paid feature in Burp.
- Web Spidering: You can passively build a website map with Spidering. This is a paid feature in Burp.
- Unthrottled Intruder: You can bruteforce login pages within OWASP as fast as your machine and the web-server can handle. This is a paid feature in Burp.
- No need to forward individual requests through Burp: When doing manual attacks, having to change windows to send a request through the browser, and then forward in burp, can be tedious. OWASP handles both and you can just browse the site and OWASP will intercept automatically. This is NOT a feature in Burp.
Task 2: Disclaimer
The documentation and support for the tool is microscopic compared to the titan that is Burp. ZAP can be used as your go-to tool to start Web Application testing but it should not be your only tool. ZAP is just one of many tools to put under your hacker utility belt.
Task 3: Installation
Download and install it from the official website: https://www.zaproxy.org/download/
In my case, I downloaded Linux Installer. Once it’s downloaded, you need to give it an execution bit (+x) and execute it to complete the installation:
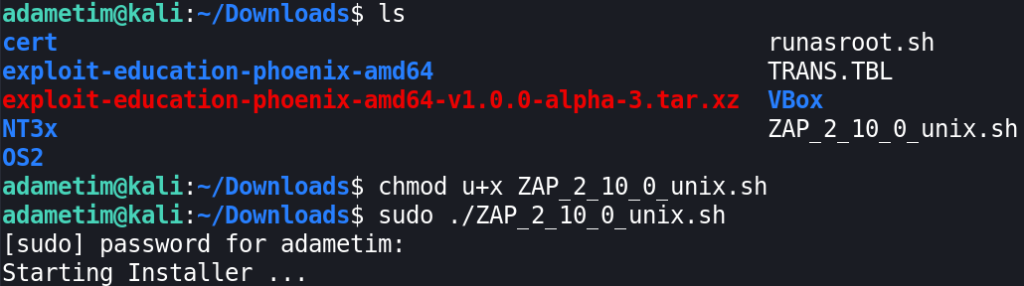
Once the installation finished, you are free to go and launch the zap application located in /usr/local/bin. You can launch it as any other program:

Task 4: How to perform an automated scan
Automated scan performs both passive and automated scans to build a sitemap and detect vulnerabilities.
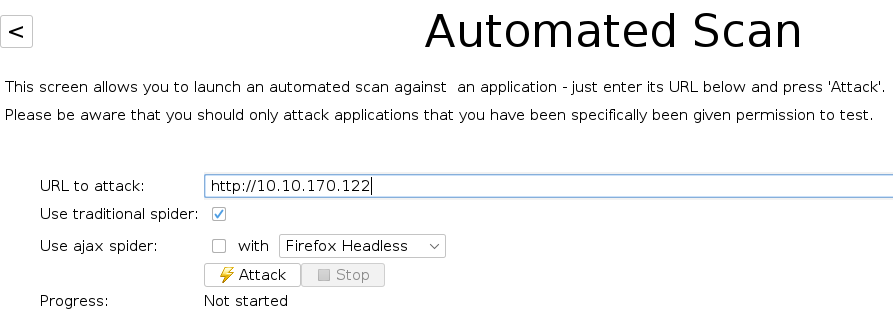
A traditional spider scan is a passive scan that enumerates links and directories of the website. It builds a website index without brute-forcing. This is much quieter than a brute-force attack and can still net a login page or other juicy details, but is not as comprehensive as a bruteforce.
The Ajax Spider is an add-on that integrates in ZAP a crawler of AJAX rich sites called Crawljax. You can use it in conjunction with the traditional spider for better results. It uses your web browser and proxy.
With a very minimal setup you are able to do an automated scan that gives you a sitemap and a handful of vulnerabilities at the bottom left:

Task 5: Manual Scanning
Like Burp, you should set-up your proxy between OWASP ZAP and your Browser. We’ll be using Firefox.
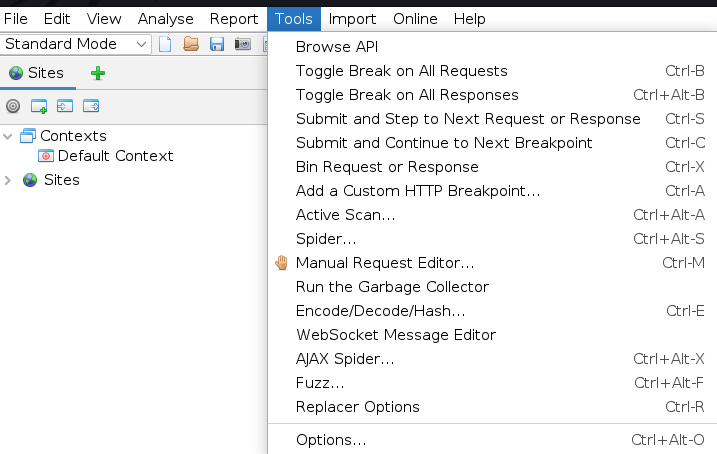
Navigate to Tools and select Options…
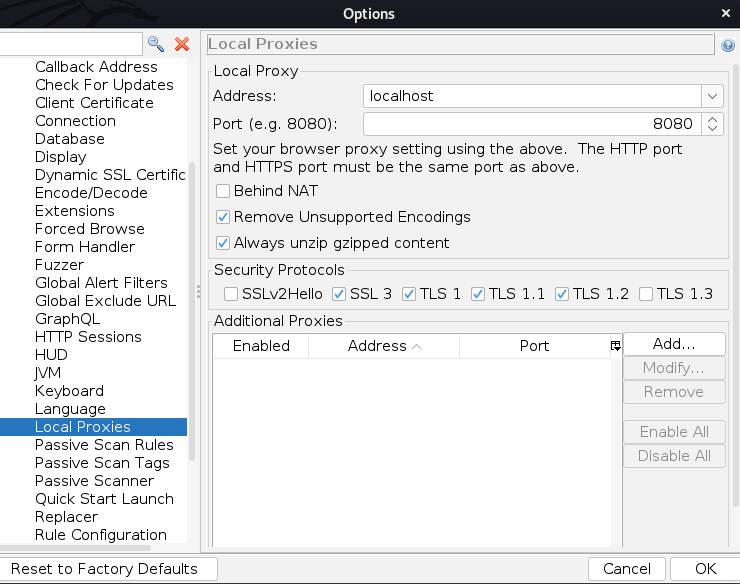
Choose an IP address (we are setting this up on our own machine, therefore localhost) and a port of your choice (8080 in my case):
Navigate to Mozilla Firefox’s Options and look for proxy settings (under Network Settings):
Select Manual proxy configuration and set it up in the same way as when configuring ZAP’s proxy:
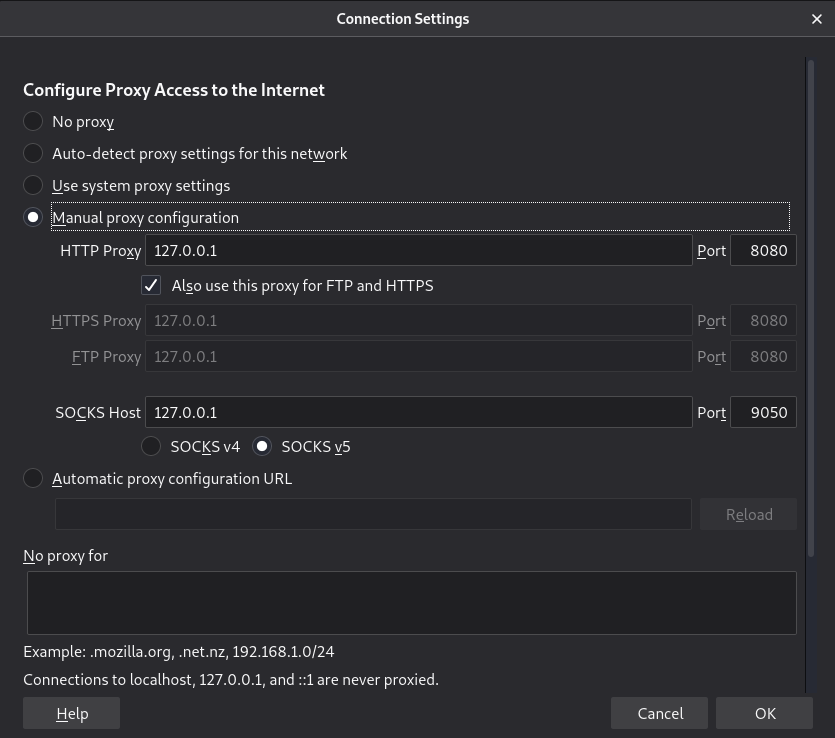
Task 6: Scanning an Authenticated Web Application
The important thing to remember is that without your ZAP application being authenticated, it can’t scan pages that are only accessible when you’ve logged in. To fully scan a webapp, you need to pass on the authentication type that the webapp uses.
So once you’ve authenticated to the webapp, hit F12 key and navigate to Storage tab:

The cookie’s value is 6cro9998nv4kv63f0bfs4ps4b5 in my case. Make a note of that.
Now back in ZAP, open the HTTP Sessions tab with the new tab button:

And set the authenticated session as active:

Now when we scan the application after these operations, the ZAP is able to pick up a lot more. This is because it’s able to see all of the sections of the webapp that were previously behind the login page.
Task 7: Brute-force Directories
You can use a wordlist attack and directory bruteforce through ZAP just as you would with gobuster. This would pick up pages that are not indexed.
Task 8: Bruteforce Web Login
When brute-forcing credentials with ZAP, you need to try to log in to the webapp and find the related HTTP GET request. Then right click on the GET request and choose Attack > Fuzz

The fuzz menu will be opened:

Select the part that you want to fuzz (in my case ‚bla‘). And the only remaining thing to do is to Add a wordlist containing payloads that will be placed to the part that you selected before.
After running the fuzzer, sort the state tab to show Reflected results first.
Task 9: ZAP Extensions
If you want to further enhance ZAP’s capabilities, look at:
https://github.com/zaproxy/zap-extensions
https://github.com/bugcrowd/HUNT
Task 10: Further Reading
The one major con of ZAP is the pitiful amount of documentation there is. The project is still active and contributed to though. Just no one’s really writing guides. So to get better at using ZAP, I will try to use it as much as possible.
I always enjoy learning about new tools that will help me in hacking. I hope you too. Thank you for reading this and see you at the next post!
I was just telling my friend about that.
Why is it I always really feel like you do?
Wonderful views on that!