Disclaimer!!!
The information provided in this blog is to be used for educational purposes only. All of the information in this blog is meant to help the reader to develop a hacker defense attitude in order to prevent the attacks discussed. In no way should you use the information to cause any kind of damage. Hacking is a crime and I am not responsible for the way you use it.
Task 1: Deploy the VM
Why can we exploit authentication bugs? Because not everyone knows how to either make proper authentication software or how to properly set up one. And sometimes, developers forget to properly sanitize a web application. Great for us!
Task 2: Dictionary attack
Dictionary attack: This is a brute-force attack that uses a combination of commonly used usernames and passwords.
To perform a dictionary attack we can either use CLI tools (Hydra, Medusa) or GUI tools (BurpSuite, ZAP). I chose to use ZAP to get more familiar with it. If you want to learn more about ZAP, please click here and read about it in one of my previous blog posts.
Let’s dive into the challenge now:
When we connect to port 8888, we can see the following web application:
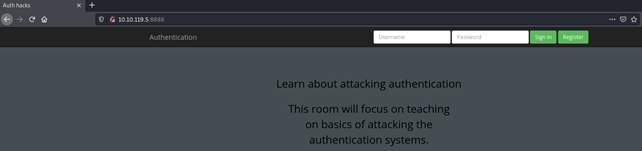
We know that username is jack so we only need to brute force the password. Let’s open up the ZAP and setup the proxy first:
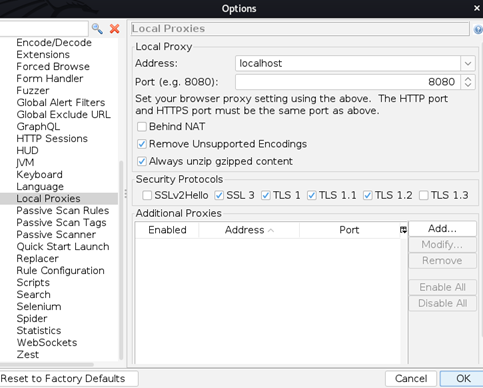
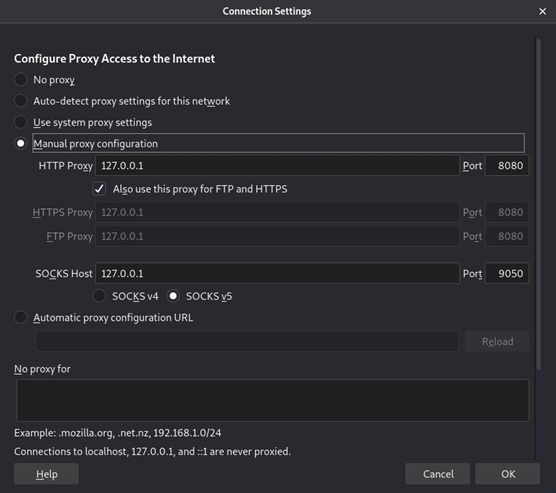
Check the HTTP History and you can see that it’s empty for now:
Let’s log in to the web application with random password. Of course it will fail:
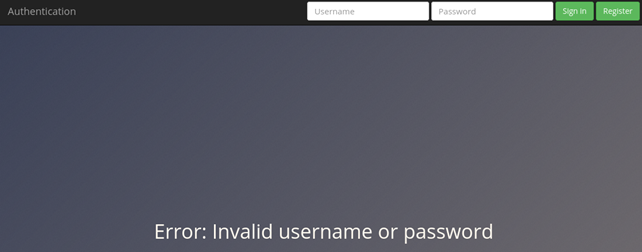
In the HTTP History, new POST record should appear:
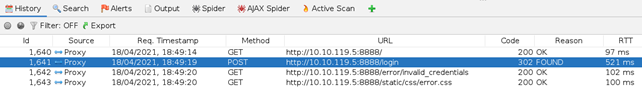
Right-click it and choose Fuzz:
Highlight the text that you want to be replaced by passwords from the dictionary and select a dictionary that you want to use. And don’t forget to use the right encoding:
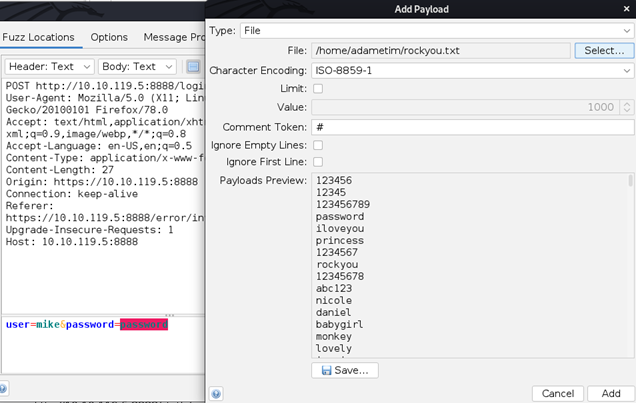
Launch the attack.
When you are in the Fuzzer tab, sort it by the Size of Response Header. And look for the entry that has the Size of Response Header a little bit higher:
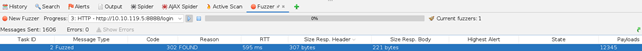
From the screenshot above you can see that the dictionary attack was successful. Copy & paste the found password:
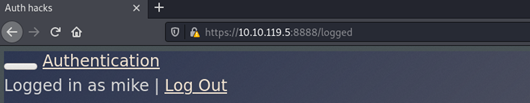
You can see that we were able to successfully log in.
Task 3: Re-registration
We are going to focus on a vulnerability that happens because of a developer’s mistake but is very easy to exploit i.e. re-registration of an existing user.
Let’s understand this with the help of an example, say there is an existing user with the name admin and now we want to get access to their account so what we can do is try to re-register that username but with slight modification. We are going to enter “ admin“(notice the space at the beginning). Now when you enter that in the username field and enter other required information like email id or password and submit that data. It will actually register a new user but that user will have the same right as normal admin. And that new user will also be able to see all the content present under the user admin.
So once again connect to port 8888. This attack should be as simple as putting a space before an existing username when registering a new user:
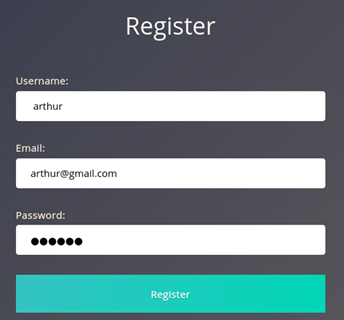
So we registered new user ‚ arthur‘. Now let’s try to log in:
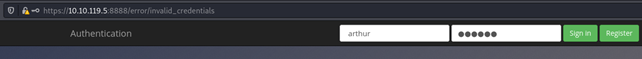
Note that you need to include the space before the username.
Now we are successfully logged in and have privileges of user arthur. If it was admin account, we would have the highest possible privileges. And that’s the goal.
Thank you for reading this. In the second part, we will look more closely at what JWT is and how to exploit it.